Computing (6)
Audience: KS2
Subject: Computing
Topic: Logical Reasoning, Algorithms, Variables, Passwords, Digital Literacy
Question: Can you write Bob’s algorithm in one line and show what the password will be for a different name and website?
Author: Reflective Thinking
Description
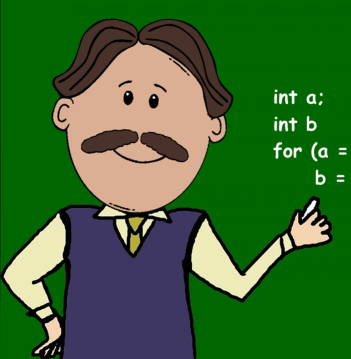
This mystery is about a simple password generation algorithm that ‘Bob’ suggested to his family that can help them create unique passwords for each family member and for each website. Through explaining how his algorithm works, ‘Bob’ explains what an algorithm is by making basic use of variables and some simple logic.
The task has been designed for the curriculum topic ‘use logical reasoning to explain how simple algorithms work’. It also provides the opportunity to refresh students’ understanding of other areas in the earlier stages of the curriculum such as algorithms and variables while they apply logical reasoning skills to understand the behaviour of an algorithm and predict its output. The mystery also demonstrates to the students how the result of the same algorithm differs based on its initial state and its input variables.
In addition to the programming-related aspects of the curriculum, the mystery also brings students’ attention to digital literacy with regards to keeping personal information private (such as passwords), and the importance of choosing strong, private, yet easy to remember passwords.
’Bob’s password algorithm’ can be used:
- To introduce new concepts such as logical reasoning
- To review topics such as algorithms and variables
- As a tool for assessing students’ understanding of algorithms, how variables are used, and how to follow up and execute an algorithm using logical reasoning
Learning outcomes:
- Use logical reasoning to understand how a simple algorithm works
- Understand variables and terms such as initial values and input variable
- Recognise that the same algorithm can produce different outputs depending on its initialization values (in this case the person’s name), and its input variables (in this case the secret number and the website name)
- Understand the importance of keeping passwords secret
- Learn some ideas on how to create their own algorithm to gene
Audience: KS3
Subject: Computing
Topic: Boolean Logic
Question: Who do you think started the fire and why?
Author: Reflective Thinking
Description
This is a ‘whodunit’ style mystery about a detective who uses ‘AND’, ‘OR’ and ‘NOT’ Boolean logic operators to help him solve a case about who started a fire and why.
Students play the role of the detective by reading witness statements to narrow down suspects from a larger input set (just as they would use these operators to narrow down search results from a very large set of input data).
Although there is no one right answer, if students combine the clues provided, with the application of simple Boolean logic, they can work out who might have been involved in different activities the night of the fire and make their own arguments as to what happened.
The mystery comes in 3 difficulty levels:
Easy
- Provides 1 witness statement for each activity (e.g. having a BBQ)
- Only by considering all the statements and applying the logic provided can students form a theory of what may have happened and why
Medium
- Provides a 2nd witness statement for each activity that doesn’t actually add any new information but provides a different logical presentation of the same thing (e.g. ‘not light hair AND not tall’ = ‘dark hair AND small’)
- This helps students understand how the same statement can be represented differently with the use of the ‘NOT’ Boolean operator
Hard
- Adds 2 more witnesses and 1 more activity (purchasing matches) to add to the complexity of the story
- Only by logically combining the statement of the two witnesses can the students know who may have bought the matches
This mystery can be used either to discuss the use of simple logical operators or as an assessment tool for students’ understanding of how to apply such simple Boolean logic to narrow down results from a larger input set.
Tips
The ‘note’ tool is ideal in this mystery for students to log the results of applying the logic of each witness statement or alternatively they could use pen and paper to write down a table of which suspects may have been involved in each activity.
All levels
- Understand the use of AND, OR, and NOT Boolean logic operators.
- Use logical reasoning to make conclusions based on a number of logical statements
- Understand different ways of representing the same logical statement with the use of the NOT operator (e.g. dark hair = NOT light hair)
- Combine more than one logical statement to find out a result
Audience: KS3
Subject: Computing
Topic: Programming Languages
Question: Should the team make a browser-based application with JavaScript and HTML or a stand-alone application (needs to be installed) with C++, and why?
Author: Reflective Thinking
Description
This mystery addresses the curriculum topic of programming languages by putting students in the role of a team of game developers. Kevin and Kate (with help from Mark and Molly) need to decide on the best option to develop their athletics game. It discusses the issue at a higher level rather than specific details about the differences between programming languages. Students are helped to understand the advantages and consequences of two types of applications: browser-based, and stand-alone.
While JavaScript, HTML and CSS is the obvious choice for browser-based applications, the choice is not that clear for stand-alone applications. However, this mystery uses C++ to make it a more realistic scenario due to it being the language mostly used for games. Nevertheless, C++ could be replaced with other languages such as Java, Python, or C# and the mystery will work equally well.
The students need to learn that with programming, compromises need to be made on the technology used. Their decision should be dependent on the features they think are the most important to have. It is useful to make the students aware that rather than picking technology first, then implementing the features supported by that technology, the better approach is to determine the features that are the most important, and then pick the technology that is suitable to implement them.
Understand:
• What browser-based applications are, the language and standards normally used to develop them, plus their advantages and disadvantages
• What stand-alone applications are, some of the common languages used to develop them, plus their advantages and disadvantages
• That in some cases compromises need to be made based on the technology used
• What the difference between HTML, CSS, and JavaScript is
Subject: Computing
Topic: Search Algorythms
Question: Which method do you think is better for finding books at the new library in the school?
Author: Reflective Thinking
Description
'Search Algorithms' addresses two key topics in the computing curriculum: understanding algorithms with sorting and searching given as examples, and comparing the utility of alternative algorithms for the same problem.
This mystery shows students that in programming, as well as in real life, there are multiple ways to solve a problem. It is important that the students realize that there is not necessarily one right approach for all cases. What works best for the scenario given in the mystery is not necessarily the best when there are fewer or more books.
The activity also shows that when designing or choosing an algorithm to solve a problem, there’s usually compromises between the time taken to learn and implement an algorithm, and the time it takes to execute an algorithm. Faster algorithms, in many cases, are harder to understand and may take more time to implement, so the choice of the algorithm depends on whether speed is critical, whether it is frequently used or not, and the time available to implement the algorithm.
You can choose between three difficulty levels in the settings. 'Easy' introduces three different approaches with their main advantages and disadvantages. 'Medium' links these algorithms to computing science, and 'Hard' gets students thinking about more challenging scenarios.
- Learn what algorithms are by using a simple formal definition supported by practical scenarios of three different algorithms to perform the same task
- Understand several key algorithms that reflect computational thinking (such as sorting, to speed up searching)
- Use logical reasoning to compare the utility of alternative algorithms for the same problem
Subject: Computing/Maths
Topic: Variables, sequences, selection
Question: What path did you have to take to get to your character’s treasure and what is the secret code to unlock it?
Author: Reflective Thinking
Description
In the form of a treasure hunt, this mystery has students follow a sequence of instructions, use and manipulate a variable, and make selections (logical decisions) based on the value of the variable.
This is a two stage mystery - students first read all of the slips, then move to the next stage in which they follow a slip-by-slip basis to find the treasure.
Each group chooses which character they want to help at the beginning of the mystery - this changes the value (the number) of marbles they start off with, and therefore, the sequence to follow and the final destination (where the treasure is). This engages students more as they can decide on the character they like the most, but also helps reflect the concept of initialisation values and how they affect the execution of any program/algorithm.
The mystery is designed to help students verify if they're following the instructions correctly or not. If they realise that they're not at the right location or that they have an incorrect number of marbles at any point, they can restart the process to identify where things went wrong.
When students believe they have reached their treasure, they can then write their answer - complete with the secret code for the lock. There are different ways you can ask them to explain how they got to the treasure. The standard would be for the students to lay out their route with slips on the screen as well as type each step of the way into their answer or even drawing it on a piece of paper.
Depending on your preferred teaching approach, the link between the programming concepts and the mystery can either be explained after the mystery to aim for the ‘aha’ moment, or before the mystery so that students are aware of their use during the hunt.
Understand:
- that what is meant by a sequence is nothing more than correctly following a set of instructions (as they did in this treasure hunt)
- the use of variables (through the marbles bag) and that they are places to store values that can be changed during the course of a computer program
- how selections are normally based on values in variables thus changing the values in such variables changes the rest of the sequence which is to be executed
- how changing the initial value of a program (the character to start with and consequently, the initial value of the variable) changes the final outcome
Subject: Computing
Topic: Network, protocol, communication, router, messaging
Question: What is the best way, or combination of ways to 1) send a warning from Peer Village to Hub Village? 2) send an invitation from Nap Village to Ack Village where they need a yes/no reply?
Author: Anne de A’Echevarria
Description
This mystery relates to the curriculum point of “Understand computer networks including the internet; how they can provide multiple services, such as the world wide web; and the opportunities they offer for communication and collaboration.”
WAN Island gets students to think about concepts in networking and especially how network protocols address different problems in networking. Users are introduced to Sam and Jo – two residents of the island. They have been asked to think of a way that villages can communicate with each other in case of attack. Students need to help consider and discuss different methods.
The rules the students will have to come up with to help people send and receive messages correctly are a network protocol. Having to come up with the rules themselves helps them understand the concept of protocols and the reasons behind them.
Teachers can explain the concepts by using elements of the story. For the devices involved in a network, each village is basically a device connected to the network and knows how to understand the network protocol. The central village will sometimes play the role of the router as it needs to receive messages addressed to other villages, retransmit them, then send the reply back and that is exactly what a router does. If the central village is connected to the internet using smoke signals, then all the villages will have smoke based internet access through the central village.
The messages to be transferred are examples of data. In the case of sound or smoke, the air is the medium just as with wireless networks. The messenger is more like a point-to-point cable based transmission (the roads/paths represent the cable).
Understand:
• that a network is one or more computing devices connected together, through the village=device analogy
• what a router is, through the use of the central village example
• what a protocol is, by having to come up with one
• that there may be different ways to transmit information but each will have its own advantages and disadvantages.
• that information can be transmitted through different media, and again, that each has its own advantages and its advantages.
For the hard set, students get introduced to basic network security concepts too.